|
|
Order by Related
- New Release
- Rate
Results in Title For modified
 | In Activision Value Publishing's Tough Trucks climb into the driver's seat of an outrageous pumped-up 4x4 and see if you can turn this right-off-the-lot machine into a genuine Modified Monster. It takes drive determination and a big dose of brain blurrin' bone rattlin' action to earn the money to convert your stock pick-up into a real track champion. Warning! You may soil your bedliner. .. |
|
Results in Keywords For modified
 | Digi-Sign is a simple program for digitally signing win32 images (Executables and DLLs) together with a simple DLL and API for validating those signatures. It is intended to provide a means of determining whether an image has been modified in any way (i.e hacked) since it was digitally signed. This can be useful if you need to ensure the integrity of your deployed files. The API is supported under both Visual C++ 6.0 and Visual Basic 6.0 and examples are provided.
Consider the following scenario. You build an application that consists of an executable and a number of DLLs. The DLLs are critical to your business model as they grant and release licenses to your application(s). In the world of hacking the DLL is easily modified to always grant licenses and your revenue stream ceases. Your application needs a means of determining whether the DLL has been modified since release. This is the capability that Digi-Sign provides... |
|
 | Sync is a simple command-line utility for performing one-way directory or file synchronization.
It synchronizes the specified target to match the specified source. Only the target is modified.
Runs on any OS with the Java Runtime Environment (JRE 6+).
Sync is free and open source software written in Java and released under the GNU GPL license (version 3).
MAIN FEATURES:
* FLEXIBLE FILE-MATCHING: Match files by combinations of name, size, last-modified time, and CRC-32 checksum; by default, (name,size,time,CRC) are used.
* FLEXIBLE FILE TIME COMPARISON: Specify a time-tolerance (in milliseconds) when matching files by their last-modified time.
* FILENAME FILTER: Use a GLOB or REGEX filter for file/directory names, or their full (relative) pathnames.
* SIMULATION MODE: Sync can be run to simulate file operations, so that the target directory is not modified.
* UNATTENDED USAGE: With an appropriate choice of switches, Sync can be executed without user intervention.
See http://syncdir.sourceforge.net/ for the latest version, screenshots, documentation, and other information...
|
|
 | Xintegrity makes it virtually impossible for anybody or anything to modify your files without being detected. When Xintegrity detects a modified file it will show exactly how and when the file was modified and display the contents of the modified file in comparison with an optionally backed up copy of the file. All your files [including operating system files] can be protected. Xintegrity can automatically create protected backup files [optionally encrypted with 256 bit AES] allowing you the option of restoring the file when modification is detected.
Auto restore and email notifications make Xintegrity ideal for monitoring large numbers of servers... |
|
 | In Activision Value Publishing's Tough Trucks climb into the driver's seat of an outrageous pumped-up 4x4 and see if you can turn this right-off-the-lot machine into a genuine Modified Monster. It takes drive determination and a big dose of brain blurrin' bone rattlin' action to earn the money to convert your stock pick-up into a real track champion. Warning! You may soil your bedliner...
|
|
 | File Modified Monitor is an easy to use utility that will inform you about modified files via email. It's a non memory resident command line application that can be typically used to monitor file modifications on unattended servers... |
|
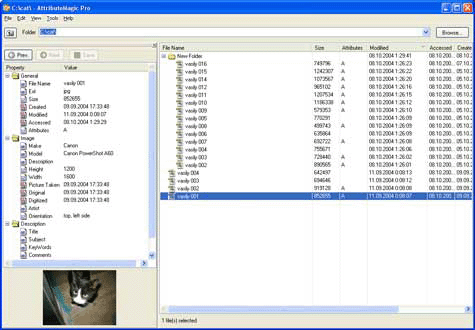 | Utility to change file/folder date-time stamps and attributes en masse. You can set or reset individual attributes, Accessed, Modified and Created dates, JPEG metadata, MS Office document dates and properties. Custom filters can be applyed to process certain items.Features list:displays and changes file and folder attributes; displays and changes file and folder date and time (Created, Modified Accessed); change properties and dates of MS Office documents. Change any property on a single file, or a group of files;set Created Date=Modified Date or Modified Date=Created Date with few mouse clicks;copy file date/time from JPEG file metadata (created by camcorders "still pictures" facility);processes one file, folder or a group of files, folders, subfolders;recursive file operations; custom file filters; pop-up calendar; easy to use, user-friendly interface;error reporting. ..
|
|
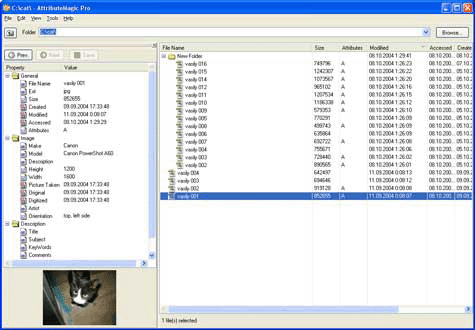 | Changes file/folder date-time stamps and attributes en masse. You can set or reset individual attributes, Accessed, Modified and Created dates, JPEG metadata, MS Office document dates and properties, NTFS data streams. Date-time shifting and masking... |
|
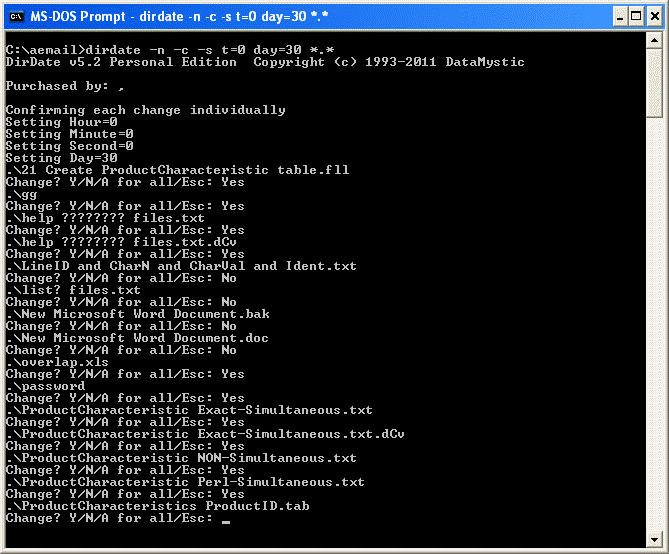 | Modify file or folder create/modify/access dates from the command line. It can change dates using either a reference file or a series of YEAR, MONTH, DAY, HOUR, MIN, SEC, MSEC commands. Handles read-only files.. |
|
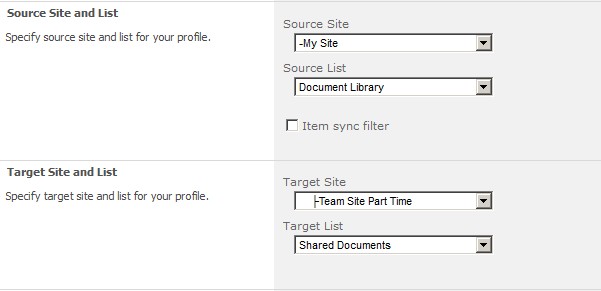 | SharePoint List Sync is an add-on feature for synchronizing document files or lists between source and target sites among SharePoint collaborators... |
|
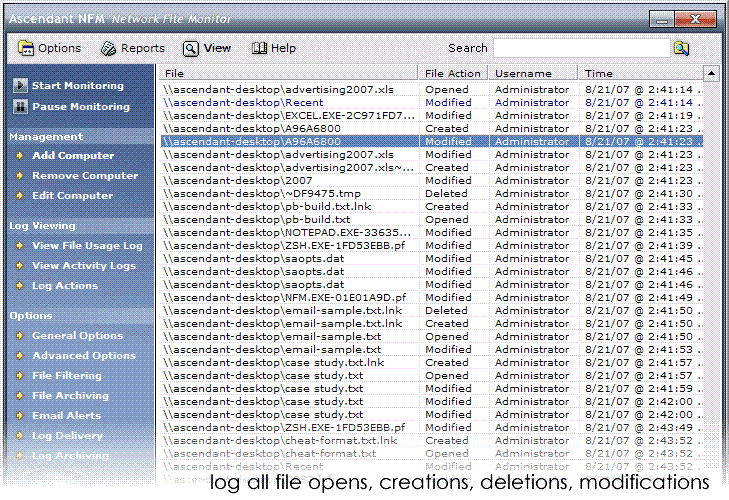 | Ascendant NFM represents the latest in cutting-edge network file monitoring security software and asset protection. While requiring absolutely no software installation on any computer on your network you can centrally monitor and record every single file action that occurs on your network. Every file creation, modification, and deletion is recorded along with the user that performed the action, and when.
Not only can Ascendant NFM monitor and log every file event that occurs on your network, but it can also protect your sensitive data and assets by archiving copies of specified files whenever they are modified, as well as alerting you whenever a user changes or deletes any critical files on your network.
BENEFITS AND USES
-Comprehensive File Monitoring
-Protect your Intellectual Property
-Secure your Network Files
-Archive all Modified Network Files
-Backup Critical Network and User Files
-Be Alerted when Files are Modified
-Track Employee and User Activities
-Prevent File and Data Theft on your Network
KEY FEATURES
-Record every file event on your network - all file creations, deletions, and changes
-Archive critical files whenever they are modified by users
-Receive instant alerts when sensitive data is altered or tampered with in any way
-Built-in log searching, filtering, and archive viewing for easy data management
-Comprehensive reporting tools, including top files used and most active users and computers
-Track user web activity by archiving web content that is downloaded
-Monitor your entire network from one central location
-Absolutely no client installations required to monitor a workstation
-100% undetectable by users - NFM does not store anything on monitored workstations.. |
|
Results in Description For modified
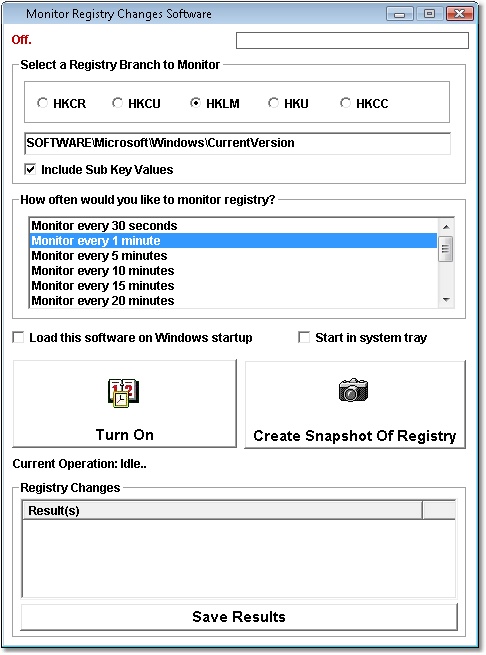 | Log changes when registry keys are created, deleted or modified... |
|
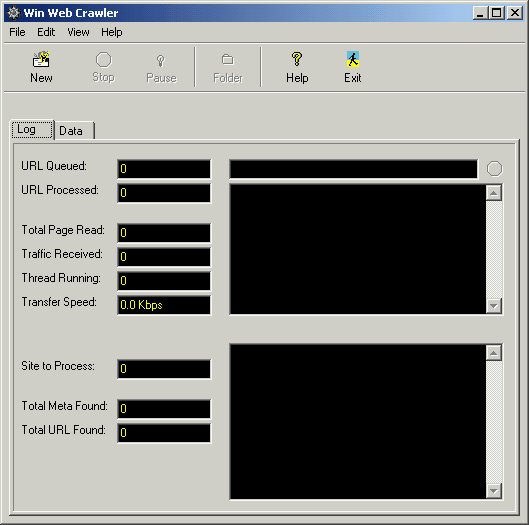 | A powerful web crawler utility for webmasters to develop search directory, web site promotion. It extracts URL, meta tag (title, desc, keyword), body text, page size, last modified date value from web site, search results or list of URLs. High speed, multi-threaded, accurate
extraction - directly saves data to disk file. Program has numerous filters to restrict
session, like - URL filter, text filter, data filter, domain filter, date modified, etc.
It allows user-selectable recursion levels, retrieval threads, timeout, proxy support
and many other options...
|
|
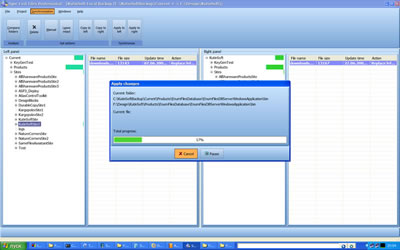 | Sync Last Files Professional is an application, which is designed for
comparing and synchronizing contents of the folders on the regular basis.
Program can compare files by date and time of last change and show only modified files.
Each project can be tuned up by these filter options:
- You can setup filtering by file masks. It helps to exclude redundant files, such as
backup copies of the documents.
- You can instruct program to include only files modified in the last X days.
- You can set maximum file size to exclude large files from comparison operation.
Sync Last Files Professional can create backup copy of each replacing or deleting file.
Also, application can mantain previous versions of backups too... |
|
 | This is simple but very usefull synchronization utility.
This program requires .NET framework.
This program can synchronize only files which were modified in the past few days. So, you can have two large folders on two computers, and you are using Flash Drive for copying files, for example. When you make some change in one of these folders you can call Sync Last Files for synchronization. It will copy only modified files to the Flash Drive. This greatly helps to synchronize big folders, which are normally can't be placed on the Flash Drive entirely.
Another great feature of this utility is capability of making incremental backups of files which are will be replaced. So you can return to any version of a file, if you incendentialy damaged last version of that file...
|
|
 | Ascendant NFM represents the latest in cutting-edge network file monitoring security software and asset protection. While requiring absolutely no software installation on any computer on your network you can centrally monitor and record every single file action that occurs on your network. Every file creation, modification, and deletion is recorded along with the user that performed the action, and when.
Not only can Ascendant NFM monitor and log every file event that occurs on your network, but it can also protect your sensitive data and assets by archiving copies of specified files whenever they are modified, as well as alerting you whenever a user changes or deletes any critical files on your network.
BENEFITS AND USES
-Comprehensive File Monitoring
-Protect your Intellectual Property
-Secure your Network Files
-Archive all Modified Network Files
-Backup Critical Network and User Files
-Be Alerted when Files are Modified
-Track Employee and User Activities
-Prevent File and Data Theft on your Network
KEY FEATURES
-Record every file event on your network - all file creations, deletions, and changes
-Archive critical files whenever they are modified by users
-Receive instant alerts when sensitive data is altered or tampered with in any way
-Built-in log searching, filtering, and archive viewing for easy data management
-Comprehensive reporting tools, including top files used and most active users and computers
-Track user web activity by archiving web content that is downloaded
-Monitor your entire network from one central location
-Absolutely no client installations required to monitor a workstation
-100% undetectable by users - NFM does not store anything on monitored workstations.. |
|
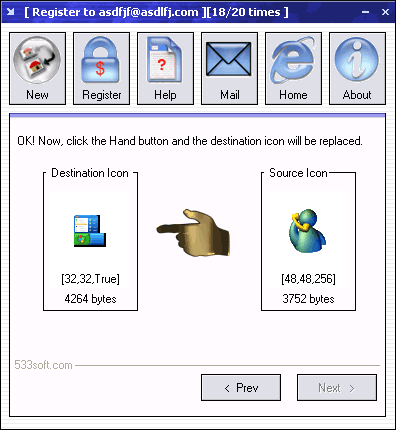 | 533soft Icon Changer can change the icon embedded in a executable or icon file. This program supports all files with the extensions .exe, .dll, .cpl, .ocx, scr, .ico. You can change the icon of these files easily and quickly. If you move the file to another computer, the new icon will be displayed anyway. The drawback is that the content of the file is modified. It results in the checksum being modified and the executable file may fail to work. Before changing the icon of a file, the Icon Changer creates a backup for that file. After changing the icon, you can run the exe file for a testing. If program can not run, you can click Undo to restore the backup file. The executable file size doesn't change. The size of the new icon should be either equal or smaller than the previous one. This software supports compressed exe file...
|
|
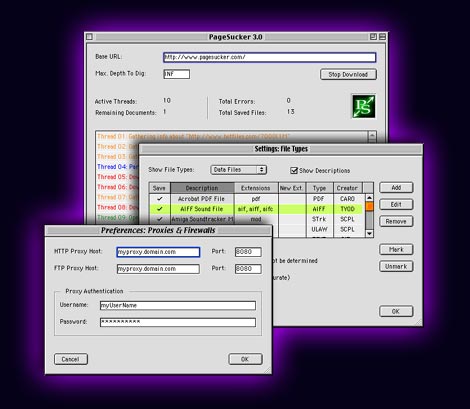 | PageSucker is a small utility that allows entire Web page hierarchies to be downloaded automatically. The pages will thereby be modified in such a way that they can then be viewed off-line (even after copying them to a CD-ROM or the like)... |
|
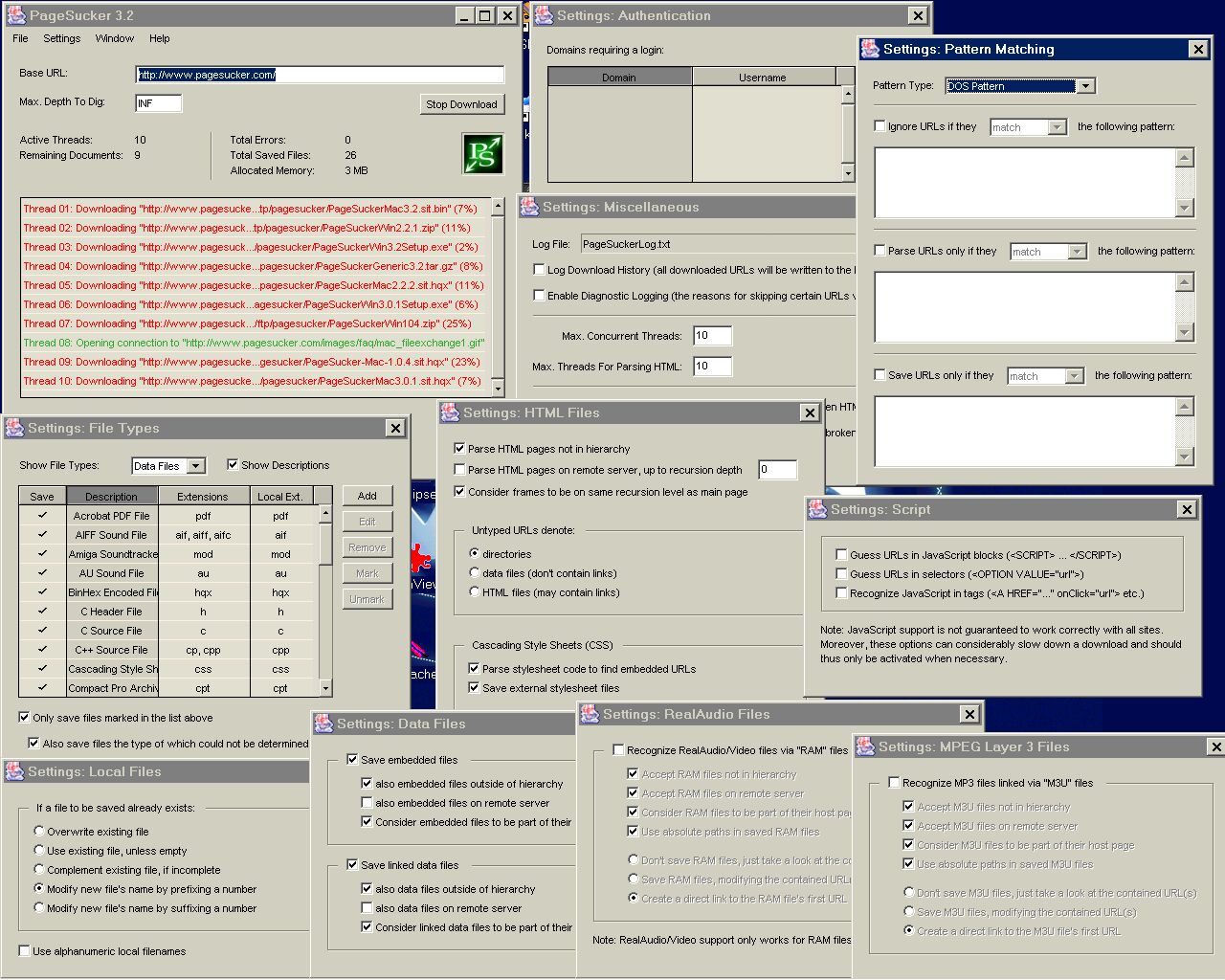 | PageSucker is a small utility that allows entire Web page hierarchies to be downloaded automatically. The pages will thereby be modified in such a way that they can then be viewed off-line (even after copying them to a CD-ROM or the like)... |
|
 | Create small (~40Kb) self-checking signature (exe-file) for folder contents. Based on SHA-1. Allows receive list of modified and removed files... |
|
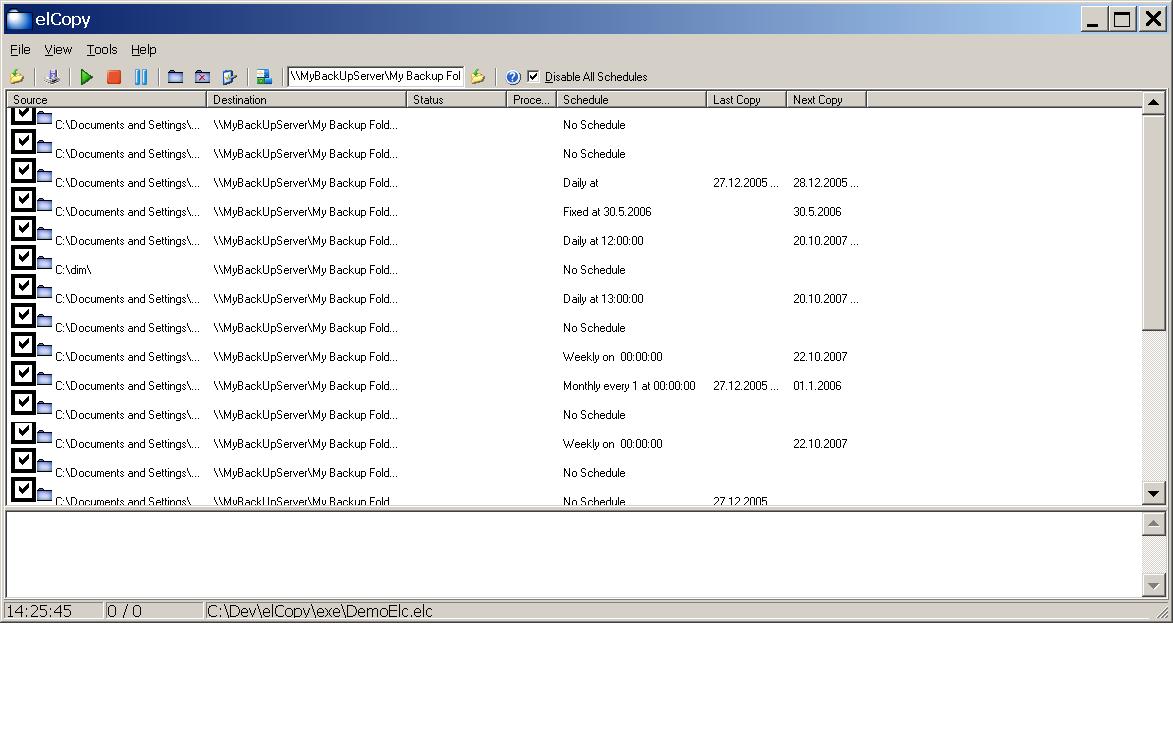 | elCopy is backup tool for making safe copies of files and folders by schedule entries , where the user can specify, different types of schedules: fixed in time, daily, hourly, weekly, monthly, schedule times. The program can copy, replicate, start custom actions by schedule defined by the user. elCopy stays in the tray bar, where quietly waits for the next scheduled time in order to do the action for easy backup, in case work files are lost. By the functionality of additional run action - before backup and or after backup the user may create additional backup actions like compressing or anything he likes. The program works with .INI style files (*.ELC) that in case of need can be modified (if needed) by 3-rd party program or script, like notepad for example. Additionally the program has a customizable language interface - each caption can be translated or modified by the customer needs. The authors constantly upgrade the Available Languages... |
|
Results in Tags For modified
 | Sync is a simple command-line utility for performing one-way directory or file synchronization.
It synchronizes the specified target to match the specified source. Only the target is modified.
Runs on any OS with the Java Runtime Environment (JRE 6+).
Sync is free and open source software written in Java and released under the GNU GPL license (version 3).
MAIN FEATURES:
* FLEXIBLE FILE-MATCHING: Match files by combinations of name, size, last-modified time, and CRC-32 checksum; by default, (name,size,time,CRC) are used.
* FLEXIBLE FILE TIME COMPARISON: Specify a time-tolerance (in milliseconds) when matching files by their last-modified time.
* FILENAME FILTER: Use a GLOB or REGEX filter for file/directory names, or their full (relative) pathnames.
* SIMULATION MODE: Sync can be run to simulate file operations, so that the target directory is not modified.
* UNATTENDED USAGE: With an appropriate choice of switches, Sync can be executed without user intervention.
See http://syncdir.sourceforge.net/ for the latest version, screenshots, documentation, and other information... |
|
 | File Modified Monitor is an easy to use utility that will inform you about modified files via email. It's a non memory resident command line application that can be typically used to monitor file modifications on unattended servers...
|
|
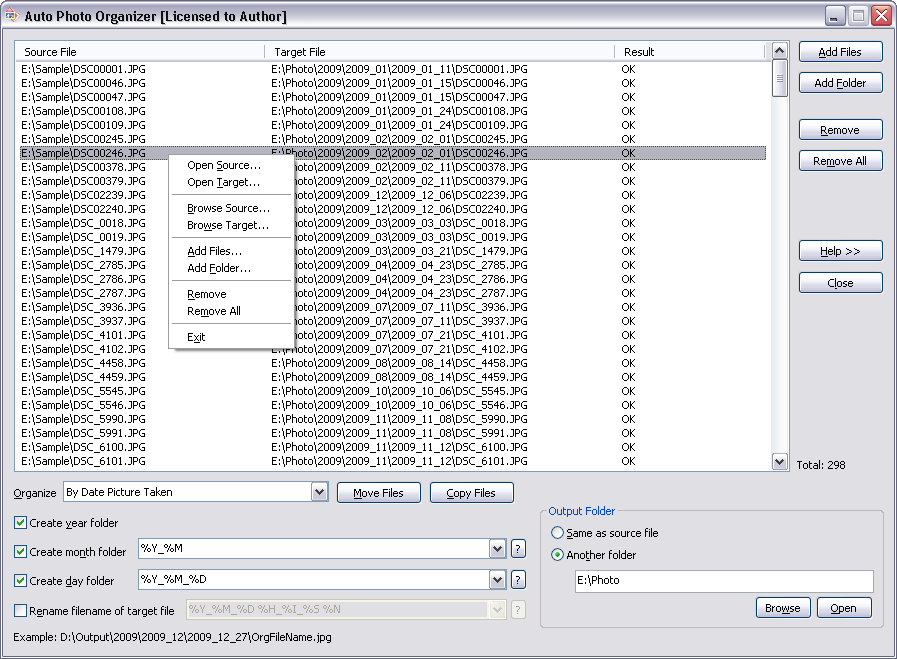 | Auto Photo Organizer organizes and renames digital photos by date picture taken, date modified, date created, and extension. The software is compatible with photos taken by major digital cameras. And it is full compatible with Vista and Windows 7... |
|
 | In Activision Value Publishing's Tough Trucks climb into the driver's seat of an outrageous pumped-up 4x4 and see if you can turn this right-off-the-lot machine into a genuine Modified Monster. It takes drive determination and a big dose of brain blurrin' bone rattlin' action to earn the money to convert your stock pick-up into a real track champion. Warning! You may soil your bedliner...
|
|
 | Modify file or folder create/modify/access dates from the command line. It can change dates using either a reference file or a series of YEAR, MONTH, DAY, HOUR, MIN, SEC, MSEC commands. Handles read-only files.. |
|
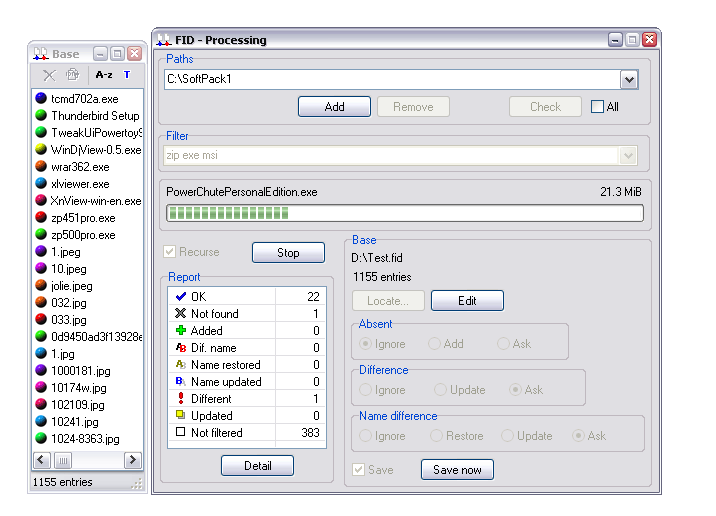 | File verification utility, uses SHA-2 algorithm...
|
|
 | Changes file/folder date-time stamps and attributes en masse. You can set or reset individual attributes, Accessed, Modified and Created dates, JPEG metadata, MS Office document dates and properties, NTFS data streams. Date-time shifting and masking... |
|
 | Utility to change file/folder date-time stamps and attributes en masse. You can set or reset individual attributes, Accessed, Modified and Created dates, JPEG metadata, MS Office document dates and properties. Custom filters can be applyed to process certain items.Features list:displays and changes file and folder attributes; displays and changes file and folder date and time (Created, Modified Accessed); change properties and dates of MS Office documents. Change any property on a single file, or a group of files;set Created Date=Modified Date or Modified Date=Created Date with few mouse clicks;copy file date/time from JPEG file metadata (created by camcorders "still pictures" facility);processes one file, folder or a group of files, folders, subfolders;recursive file operations; custom file filters; pop-up calendar; easy to use, user-friendly interface;error reporting. .. |
|
 | Okoker Encrypt Folder is a secure and easy to use program that lets you password-protect and easily prevent access to your important folders.A protected folder and its contents will be prevented from being renamed, modified, deleted, copied, moved, accessed or even seen on the system.You can only enter the system by using the correct password, which will enable you to view or edit the encrypted folder contents. Wherever, at home, work, or any other environment where you share your computer with others, Okoker Encrypt Folder can really help you secure your files and folders from prying eyes, malicious programs, users, and getting infected by dangerous viruses and unwanted access or accidental damage. The Encrypt Folder interface has been designed to be intuitive and easy to use , and the most important is that the software is human and intelligent .
Super drag and drop to quickly Encrypt or Decrypte your folders... |
|
 | Another script for your church site: this allows your congregation to read through the Bible in a year, either by visiting your site each day, or subscribing to the RSS feed... |
|
Related search : heck forcommand linemodified files,photo organizerauto photosoftware coulddate createdmodified datedate accessedorganizer softwaredate takendate modified,auto photo organizerdate modified datemodified date createdsoftware could organizephoto organizeOrder by Related
- New Release
- Rate
modified food starch -
psp modified software -
modified ford cars -
genetically modified corn -
recently modified files -
|
|



















