|
|
Order by Related
- New Release
- Rate
Results in Title For aileen wuornos execution
 | This shareware allows you to encrypt/lock, decrypt/unlock files and folders, based on your needs. You also could use this shareware to run an encrypted file or encrypted folder of your chosen, and the file or folder in question remains encrypted/locked after the execution. Moreover, this is a fully functional 30-day shareware. Try it now! .. |
|
Results in Keywords For aileen wuornos execution
 | SmartChart provides a simple solution for creating and displaying graphs from within Windows and web applications. The communication with SmartChart is done via a text file. SmartChart supports batch execution that enables execution of a set of commands, with or without opening the main application window. Using batch execution, you can generate several graphs and redirect the output into different output channels, such as a printer, the clipboard, a Jpeg file or a BMP file. SmartChart provides a friendly interface that the end users can master in no .. |
|
 | This shareware allows you to encrypt/lock, decrypt/unlock files and folders, based on your needs. You also could use this shareware to run an encrypted file or encrypted folder of your chosen, and the file or folder in question remains encrypted/locked after the execution. Moreover, this is a fully functional 30-day shareware. Try it now!..
|
|
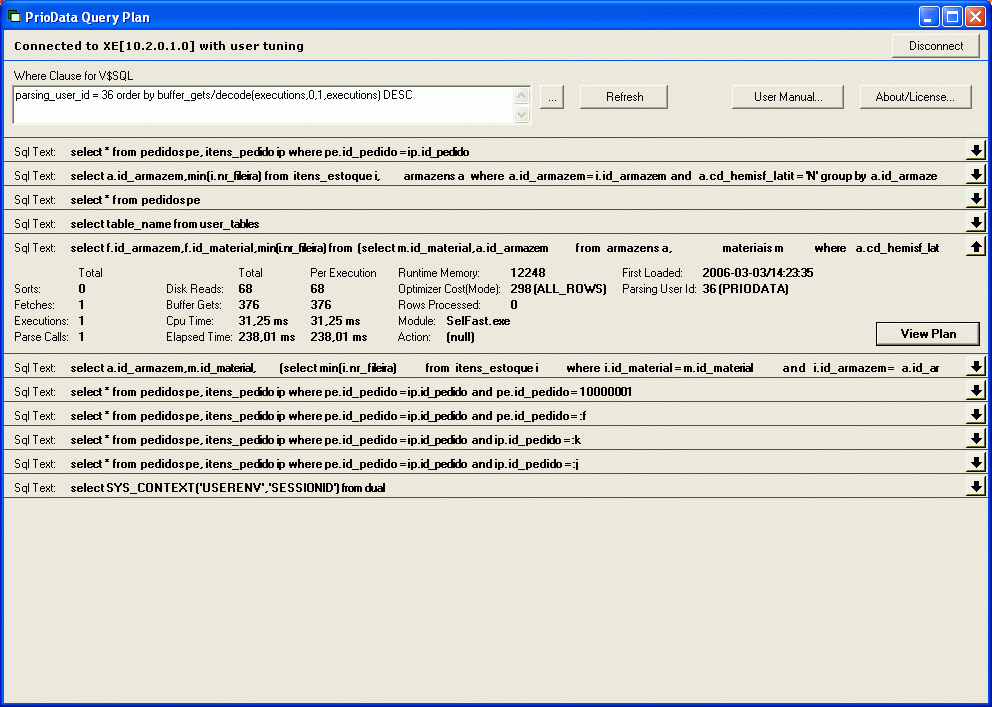 | A tool to browse Oracle's library cache to locate SQL statement to tune. Shows the execution plan in the classical hierarquical view, shows complete SQL text (without having to write complex joins to V$SQLTEXT). Compatible with Oracle 9i and later... |
|
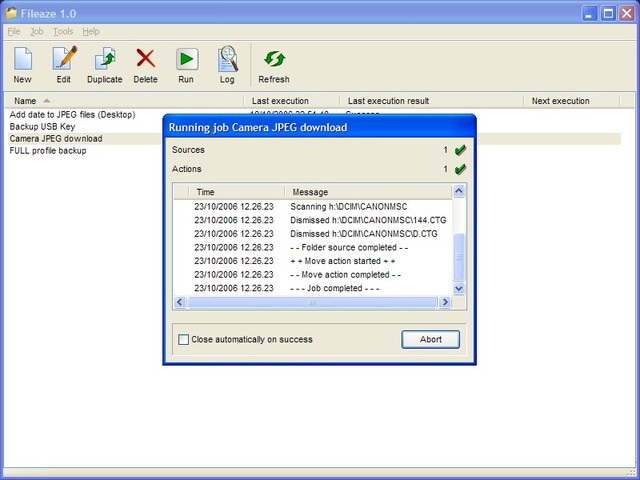 | Fileaze is a batch tool for recurrent file manipulation tasks. It allows you to execute sequences of operations on a collection of files gathered from folders, FTP servers, e-mail attachments and web pages. Fileaze can copy, move, rename, delete, change attributes and dates of these files. It supports text replacement, zip/unzip operations, encryption and decryption of collected files and it can also upload them to FTP servers or send them out as e-mail attachments. You can even invoke external commands or applications with your files passed along as parameters allowing you to have access to your favourite tools from within your jobs. Fileaze supports Regular Expressions in pattern matching to help you fine-tune your file selection. Fileaze lets you select files from multiple locations within a single job so you can easily automate complex and tedious manual tasks by turning them into smart jobs. Scheduled execution of batch jobs is also supported to make them run in the background at a fixed time, preset interval or upon occurrence of events. Fileaze supports parameterized execution through a set of predefined and custom constants helping you to customize your job at execution time thus allowing you to reuse the same job in multiple scenarios. By combining all these features you can create batch jobs ranging from the simple to the most sophisticated. Fileaze can become a backup tool or a mirroring application. You can turn it into an automatic digital photo downloader that creates date-based folders for smart photo organization. It can work as an upstreaming daemon that automatically publishes modified files on the Web via FTP becoming a Web renderer or an online collaboration tool. You can periodically encrypt sensible files and upload them to a remote server as an emergency backup or you could just set Fileaze up to be a time-based Web downloader for always up to date retrieval. Fileaze helps you get things done...
|
|
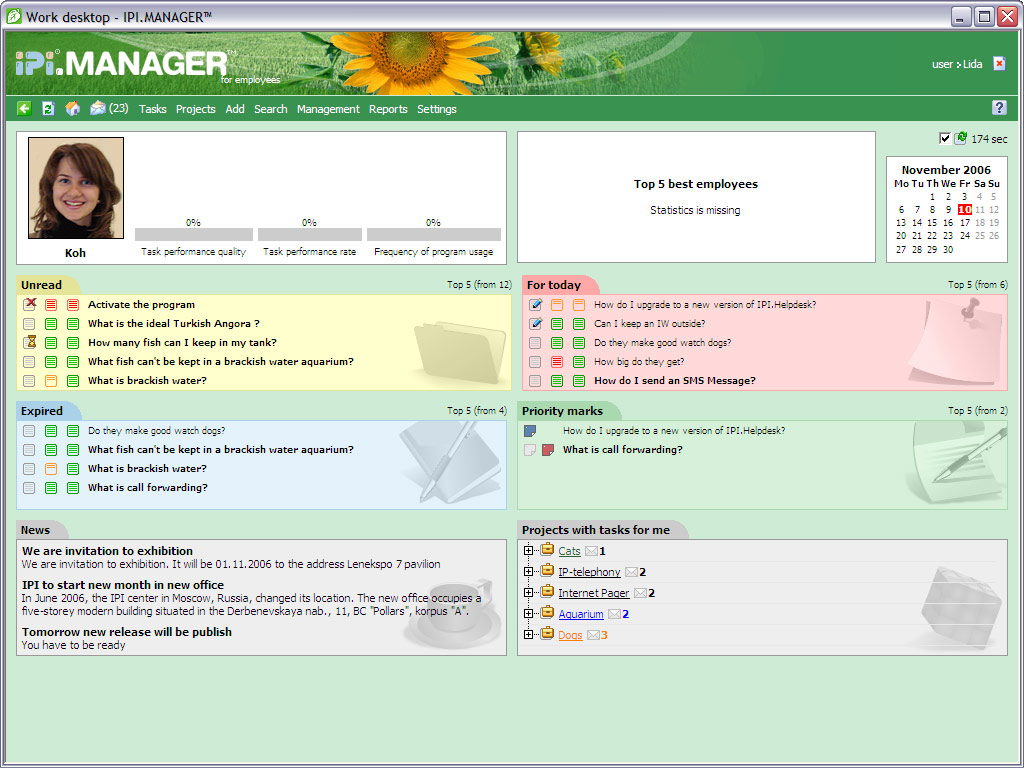 | Task management systems are now widely used in large organizations, and they require a thorough, systematized approach to implementation and deployment. In the SMB market, however, systems such as HelpDesk, ServiceDesk or TaskManager are very rare, because of the high cost of the software and the complexity of configuration and customization.
7 reasons for choosing IPI.MANAGER:
1. .. |
|
 | Exe Wrapper allows you to protect any Exe-file with its own password from non- authorized execution.
And it can modify the main icon of the .exe file. If you mean to keep people out of your personal stuff, add or modify the icon of executable fil..
|
|
 | The Component Inspector allows you to inspect and execute any .NET code (application, class, or component). The inspector includes the following: Event Logging - View the events generated as a result of the execution of any object. Examine the all event information related including the stack trace and event object; Visual Design Surface - Examine and modify the behavior of visual components at both design and runtime. Construct arbitrary combinations of controls; Object Browser - Examine and modify the contents of any objects; Method Execution - Execute methods on any object; Drag/Drop Object Creation - Create an object of any type; Intelligent Object Browsing - Presents common classes (IList, etc) without internal details, allowing you to easily and directly access the contents; Direct Execution - Directly execute any application, class or control without writing any code... |
|
 | Software protection tool. Its purpose is to selectively encrypt fragments of code in the program and add special code for stop debugging and disassembling. Features include:- polymorphic encryption with no constant signatures in encrypted fragments; - encrypted fragment will only be decrypted immediately before its execution; after the execution of the particular fragment it will be encrypted again (at any time during the execution there is only one protected fragment decrypted) - encryption has unlimited nesting (encrypted block inside encrypted block inside...) - single-use fragments: it is possible to mark a fragment of code so that fragment will be erased after the very first execution - user-key encryption - detect SoftIce, NtIce, FrogIce, TD and other debugger - detect registry/filesystem/API monitors - counteraction to dumping application with tools like ProcDump - anti-tracing measures - anti-disassembler measures - direct WinAPI support working around import table. - full integration with HardKey registration keymanager EXECryptor can protect any 32bit PE executable files. It was tested under W95/98/ME/2000/NT/XP. SDK available for Delphi, CBuilder, MSVC. .. |
|
 | EMS SQL Query for DB2 is a useful tool that lets you quickly and simply build SQL queries to IBM DB2 databases. Visual DB2 query building as well as direct editing of a query text is available... |
|
 | This multi-faceted template provides for all these aspects of the testing cycle. It guides you through the entire process with in-depth suggestions all along the way. In addition, it specifically does this for the Lotus Notes environment!.. |
|
Results in Description For aileen wuornos execution
 | ActiveX OCX to compress files in the Bzip2 format , ability to pause , resume and cancel the compression execution , the compression code is loaded dinamically in the process of the software using the control ,the control can provide progress information about the compression and decompression functions , the code execution is optimized for speed.. |
|
 | RSP MP3 OGG Vorbis Encode OCX 1.4.0 is an ActiveX OCX to convert wav to MP3 and OGG Vorbis format, The encode process occurs in an out-of-process environment , so , the control can have all the control over the process running ,the speed execution is faster than similar encode tools, with the ability to pause , resume and cancel the encode execution..
|
|
 | Software protection tool. Its purpose is to selectively encrypt fragments of code in the program and add special code for stop debugging and disassembling. Features include:- polymorphic encryption with no constant signatures in encrypted fragments; - encrypted fragment will only be decrypted immediately before its execution; after the execution of the particular fragment it will be encrypted again (at any time during the execution there is only one protected fragment decrypted) - encryption has unlimited nesting (encrypted block inside encrypted block inside...) - single-use fragments: it is possible to mark a fragment of code so that fragment will be erased after the very first execution - user-key encryption - detect SoftIce, NtIce, FrogIce, TD and other debugger - detect registry/filesystem/API monitors - counteraction to dumping application with tools like ProcDump - anti-tracing measures - anti-disassembler measures - direct WinAPI support working around import table. - full integration with HardKey registration keymanager EXECryptor can protect any 32bit PE executable files. It was tested under W95/98/ME/2000/NT/XP. SDK available for Delphi, CBuilder, MSVC. .. |
|
 | The Component Inspector allows you to inspect and execute any .NET code (application, class, or component). The inspector includes the following: Event Logging - View the events generated as a result of the execution of any object. Examine the all event information related including the stack trace and event object; Visual Design Surface - Examine and modify the behavior of visual components at both design and runtime. Construct arbitrary combinations of controls; Object Browser - Examine and modify the contents of any objects; Method Execution - Execute methods on any object; Drag/Drop Object Creation - Create an object of any type; Intelligent Object Browsing - Presents common classes (IList, etc) without internal details, allowing you to easily and directly access the contents; Direct Execution - Directly execute any application, class or control without writing any code...
|
|
 | UncleOra for Oracle is a multi-threaded SQL and PL/SQL tool with a script library and an advanced grid for developers and database administrators. Features: script library; SQL and PL/SQL editor; single, multiple and for update statement execution; bind variables; commands EXECUTE and DESCRIBE; powerful grid; SQL statement execution plan; popup window with database objects; script import; transaction queue; oracle home selector... |
|
 | This tool will help to remove the MyDoom.A and My.Doom.B worms from infected Windows XP and Windows 2000 systems. Once executed, the tool automatically checks for infection and removes the worm(s) if any. If a machine is infected with MyDoom.B, the tool will also provide the user with the default version of the "hosts" file and set the "read-only" attribute for that file. This action will allow the user to visit previously-blocked Microsoft and antivirus websites. After execution, the tool pops-up a message describing the outcome of the detection/removal. The tool can be safely deleted after execution. Also, the tool creates a log file named doomcln.log in the %WINDIR%debug folder.This tool will not:..
|
|
 | SecuriTask 2005 monitor and prevents task execution before they are
loaded by the system. You can also :
Manage lists of allowed or blocked programs.
Repair an infected computer with only one reboot by blocking
malicious or useless programs.
Lock services creation and modification
Monitor Internet explorer for DLL loading to prevent all
unwanted toolbar (adware)
2 modes : interactive mode ask you just before each process
creation instead of secure mode which only allow execution
of trusted programs (the best way for network administrators
to prevent unwanted usage of computer...)
- Low level monitoring (kernel)
- Filtered extension :
*.COM *.EXE *.PIF *.SCR *.BAT *.CMD *.VBS *.VBE *.JS *.JSE *.WSF
*.WSH and more...
- Prevents also script running like VbScript, JavaScript, Windows script...
- Locks Services creation and modification.
- Monitors and intercepts tasks launched by user or by system.
- Monitors and blocks process execution initiated by another allowed
task.
- Blocks execution before process creation (instead of other security
programs which kill the task once the system has launched it).
- Monitors Internet Explorer extension loading to prevent ad-ware or
unwanted toolbar.
- Password protected in secure mode. (for network administrator)
- Uninstallation protected with password.
- Choice of two languages (French or English).. |
|
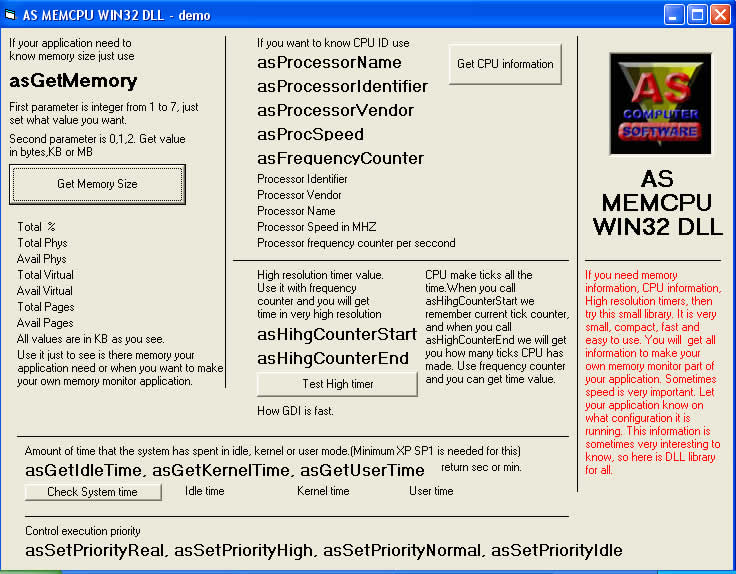 | Get all data for CPU. Know how is memory used.Control priority of execution. Use high resolution timer... |
|
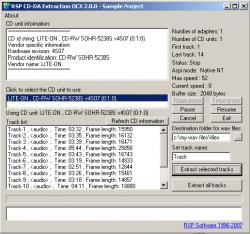 | ActiveX OCX to list , test and extract audio or data from CD units and save as wav PCM files - Ability to test the CD hardware - Ability to extract audio ( or data! ) and save as PCM wav file- Ability to report information about the CD units hardware - Ability to pause , resume and cancel the extraction execution - The execution occurs in an additional thread running concurrently with the main thread.. |
|
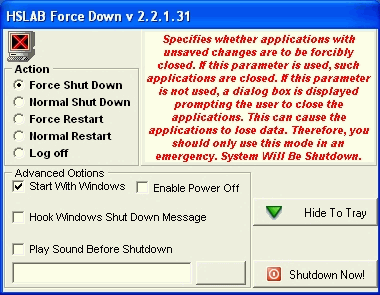 | The program is intended for fast and guaranteed execution of Windows Shutdown if there is a plenty of open applications... |
|
Results in Tags For aileen wuornos execution
 | This shareware allows you to encrypt/lock, decrypt/unlock files and folders, based on your needs. You also could use this shareware to run an encrypted file or encrypted folder of your chosen, and the file or folder in question remains encrypted/locked after the execution. Moreover, this is a fully functional 30-day shareware. Try it now!.. |
|
 | Fileaze is a batch tool for recurrent file manipulation tasks. It allows you to execute sequences of operations on a collection of files gathered from folders, FTP servers, e-mail attachments and web pages. Fileaze can copy, move, rename, delete, change attributes and dates of these files. It supports text replacement, zip/unzip operations, encryption and decryption of collected files and it can also upload them to FTP servers or send them out as e-mail attachments. You can even invoke external commands or applications with your files passed along as parameters allowing you to have access to your favourite tools from within your jobs. Fileaze supports Regular Expressions in pattern matching to help you fine-tune your file selection. Fileaze lets you select files from multiple locations within a single job so you can easily automate complex and tedious manual tasks by turning them into smart jobs. Scheduled execution of batch jobs is also supported to make them run in the background at a fixed time, preset interval or upon occurrence of events. Fileaze supports parameterized execution through a set of predefined and custom constants helping you to customize your job at execution time thus allowing you to reuse the same job in multiple scenarios. By combining all these features you can create batch jobs ranging from the simple to the most sophisticated. Fileaze can become a backup tool or a mirroring application. You can turn it into an automatic digital photo downloader that creates date-based folders for smart photo organization. It can work as an upstreaming daemon that automatically publishes modified files on the Web via FTP becoming a Web renderer or an online collaboration tool. You can periodically encrypt sensible files and upload them to a remote server as an emergency backup or you could just set Fileaze up to be a time-based Web downloader for always up to date retrieval. Fileaze helps you get things done...
|
|
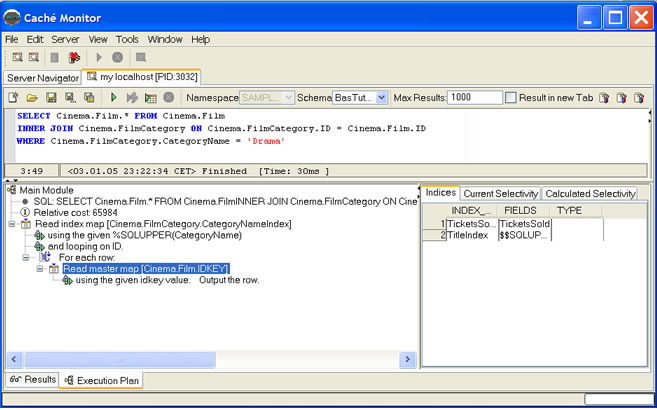 | Cache Monitor is the SQL development tool designed for InterSystems database Cache. It supports developers with features, like: advanced SQL Query Editor,Cache-SQL Syntax highlighting,SQL Code completion,SQL History buffer for executed SQL commands,SQL Code formatting,Graphical SQL execution plan and more... |
|
 | If you have ever used RunAs utility, which is supplied together with the Windows, then SafeLauncher is the best choice for you. SafeLauncher may be considered as the container for the applications you usually use. You may add any application into this container and execute it under the required account. It has a nice user interface and provides you with a fast and simple way of running the applications. Use the icon in the system tray, the main window of SafeLauncher or shortcut to run the application from the container. When you minimize SafeLauncher it disappears leaving the icon in the system tray. This icon may be used for fast execution of any application in the container. Context help together with detailed documentation will make your acquaintance with SafeLauncher quick and easy.
People often work on their computers under the account which belongs to the local administrators group. But not everybody realizes that any program he or she runs may do whatever it wants with their data. For instance, when you run the Internet Explorer you believe that it has nothing to do with your data, but due to vulnerabilities inside it there is a chance that some malicious code downloaded from the web site could be executed inside the Internet Explorer. So we end up with a 'malicious program' running on your computer with unlimited privileges. Sure the antivirus software can detect that and fire an alarm, but most of the time this happens with well known malicious code and the antivirus has nothing to do with the code which it sees for the first time. In this case, a better solution is to run the Internet Explorer under the account that doesn't belong to the administrators group and has fewer privileges than the account you are usually working under. So even if the malicious code gets executed it will fail to steal any data or infect your computer. In the worst case the Internet Explorer application gets crashed...
|
|
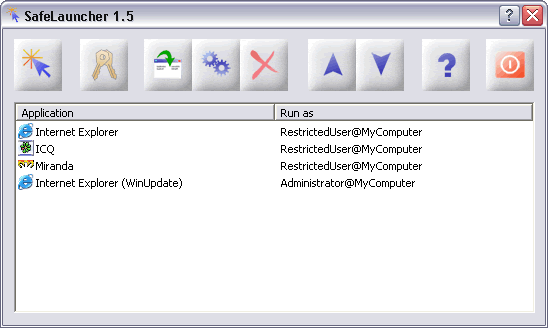 | If you have ever used RunAs utility, which is supplied together with the Windows, then SafeLauncher is the best choice for you. SafeLauncher may be considered as the container for the applications you usually use. You may add any application into this container and execute it under the required account. It has a nice user interface and provides you with a fast and simple way of running the applications. Use the icon in the system tray, the main window of SafeLauncher or shortcut to run the application from the container. When you minimize SafeLauncher it disappears leaving the icon in the system tray. This icon may be used for fast execution of any application in the container. Context help together with detailed documentation will make your acquaintance with SafeLauncher quick and easy.
People often work on their computers under the account which belongs to the local administrators group. But not everybody realizes that any program he or she runs may do whatever it wants with their data. For instance, when you run the Internet Explorer you believe that it has nothing to do with your data, but due to vulnerabilities inside it there is a chance that some malicious code downloaded from the web site could be executed inside the Internet Explorer. So we end up with a 'malicious program' running on your computer with unlimited privileges. Sure the antivirus software can detect that and fire an alarm, but most of the time this happens with well known malicious code and the antivirus has nothing to do with the code which it sees for the first time. In this case, a better solution is to run the Internet Explorer under the account that doesn't belong to the administrators group and has fewer privileges than the account you are usually working under. So even if the malicious code gets executed it will fail to steal any data or infect your computer. In the worst case the Internet Explorer application gets crashed... |
|
 | SQL Edge not only allows users to execute SQL scripts, but also provides a powerful way to visualize data relationships. With SQL Edge, users can use only one query to retrieve data in a master table, and then browse data in all related detail tables..
|
|
 | Task management systems are now widely used in large organizations, and they require a thorough, systematized approach to implementation and deployment. In the SMB market, however, systems such as HelpDesk, ServiceDesk or TaskManager are very rare, because of the high cost of the software and the complexity of configuration and customization.
7 reasons for choosing IPI.MANAGER:
1. .. |
|
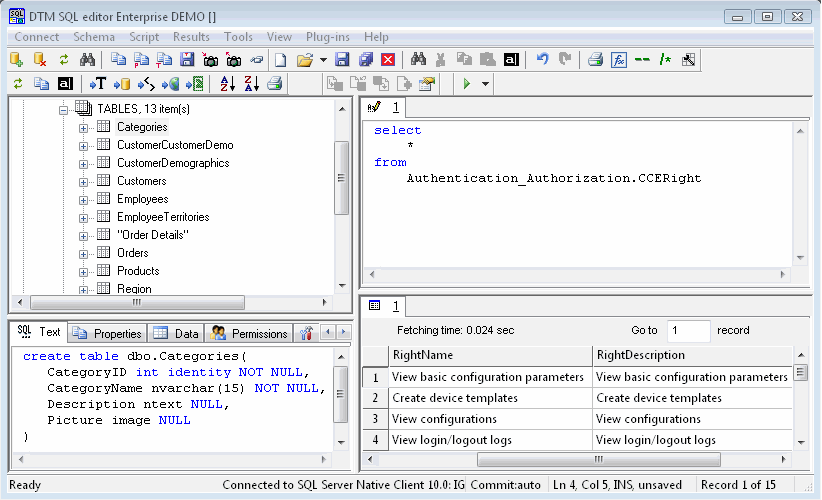 | DTM SQL editor is a set of powerful database management tools that allow you to have unified access to different types of databases and to have a set of solutions that makes processing your data easy. Get your free demo version now... |
|
 | Software protection tool. Its purpose is to selectively encrypt fragments of code in the program and add special code for stop debugging and disassembling. Features include:- polymorphic encryption with no constant signatures in encrypted fragments; - encrypted fragment will only be decrypted immediately before its execution; after the execution of the particular fragment it will be encrypted again (at any time during the execution there is only one protected fragment decrypted) - encryption has unlimited nesting (encrypted block inside encrypted block inside...) - single-use fragments: it is possible to mark a fragment of code so that fragment will be erased after the very first execution - user-key encryption - detect SoftIce, NtIce, FrogIce, TD and other debugger - detect registry/filesystem/API monitors - counteraction to dumping application with tools like ProcDump - anti-tracing measures - anti-disassembler measures - direct WinAPI support working around import table. - full integration with HardKey registration keymanager EXECryptor can protect any 32bit PE executable files. It was tested under W95/98/ME/2000/NT/XP. SDK available for Delphi, CBuilder, MSVC. .. |
|
 | The Component Inspector allows you to inspect and execute any .NET code (application, class, or component). The inspector includes the following: Event Logging - View the events generated as a result of the execution of any object. Examine the all event information related including the stack trace and event object; Visual Design Surface - Examine and modify the behavior of visual components at both design and runtime. Construct arbitrary combinations of controls; Object Browser - Examine and modify the contents of any objects; Method Execution - Execute methods on any object; Drag/Drop Object Creation - Create an object of any type; Intelligent Object Browsing - Presents common classes (IList, etc) without internal details, allowing you to easily and directly access the contents; Direct Execution - Directly execute any application, class or control without writing any code... |
|
Related search : internet explorermalicious code,internet explorermalicious code,sql edge,ipi managerfull control,dtm sqlsql editorsql statements,encrypted block insidedevelopment software downloadsoftcomplete development softwarecomponent inspector,net component insOrder by Related
- New Release
- Rate
process execution -
execution plan -
execution environment -
code execution -
nazi execution -
|
|
















